
TrustONE‘s “Stealth Defense” protects critical operational server files, including:
- Database Server
- Backup Server (Acronis/Commvault/Veeam/Veritas)
- Web Server
- AD GPO
- Hyper-V
The diagram below illustrates the example of protecting an SQL database:
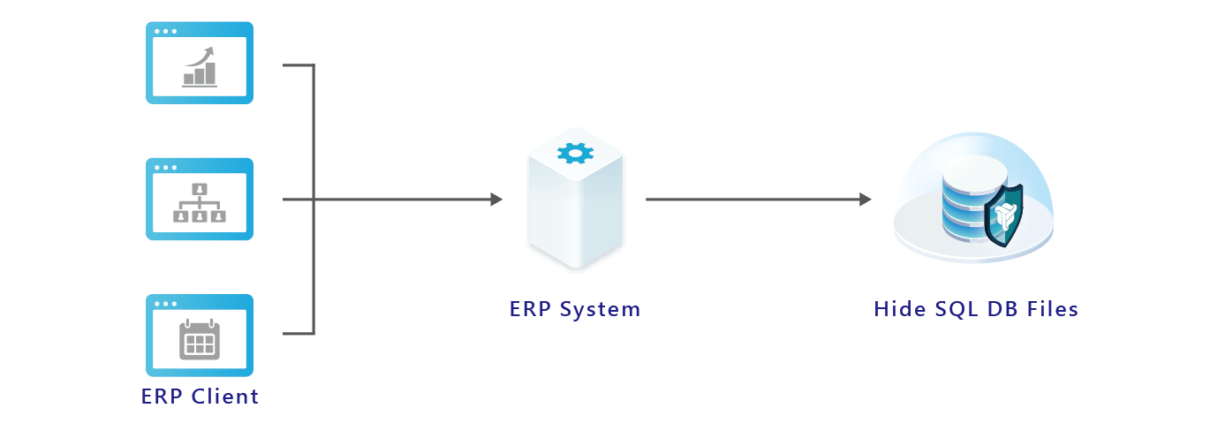
It sets these important folders as “Stealth Protected Zones,” where legitimate users can access them normally, but hackers and ransomware cannot see or attack the protected areas. This prevents encryption, data theft, or malicious alteration of crucial files.
For more detailed information, please refer to the video link below:
TrustONE Stealth Defense Technology – Backup Protection

TrustONE’s “Security Broker” targets security vulnerabilities in unprotected operational servers by providing server stealth, isolating servers in protected zones, implementing two-factor authentication (OTP) for system administrators, and deploying decoy systems to track and capture hackers (providing threat intelligence on attack sources).
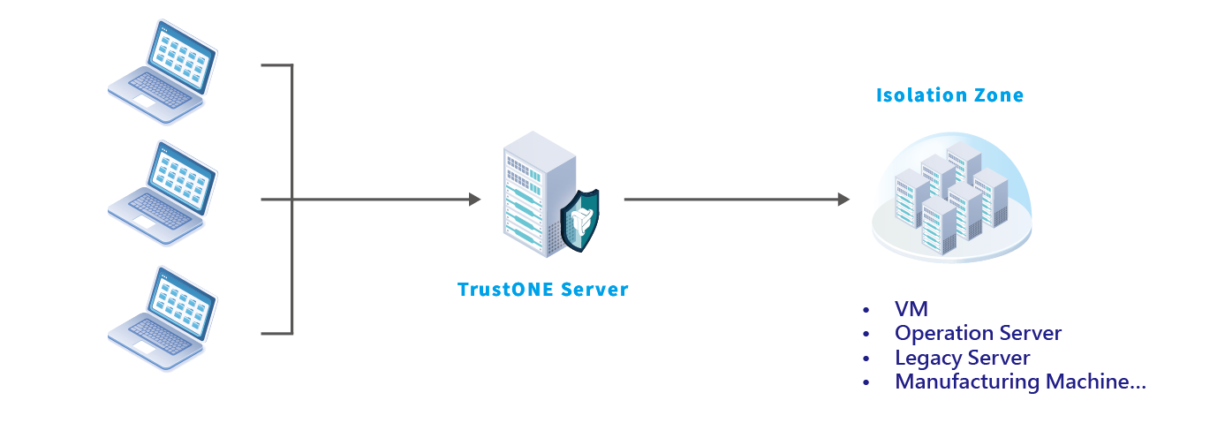
For more detailed information, please refer to the video link below:
TrustONE VM Attack and Defense Simulation
https://youtu.be/9NcUcU6hppY

